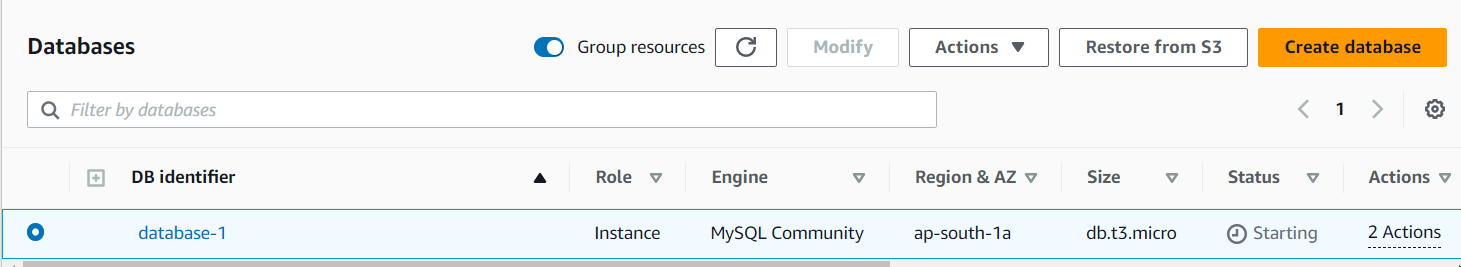
1. Open the AWS Management Console: Go to the AWS Management Console and log in to your AWS account.
2. Choose RDS: From the list of AWS services, choose RDS (Relational Database Service).
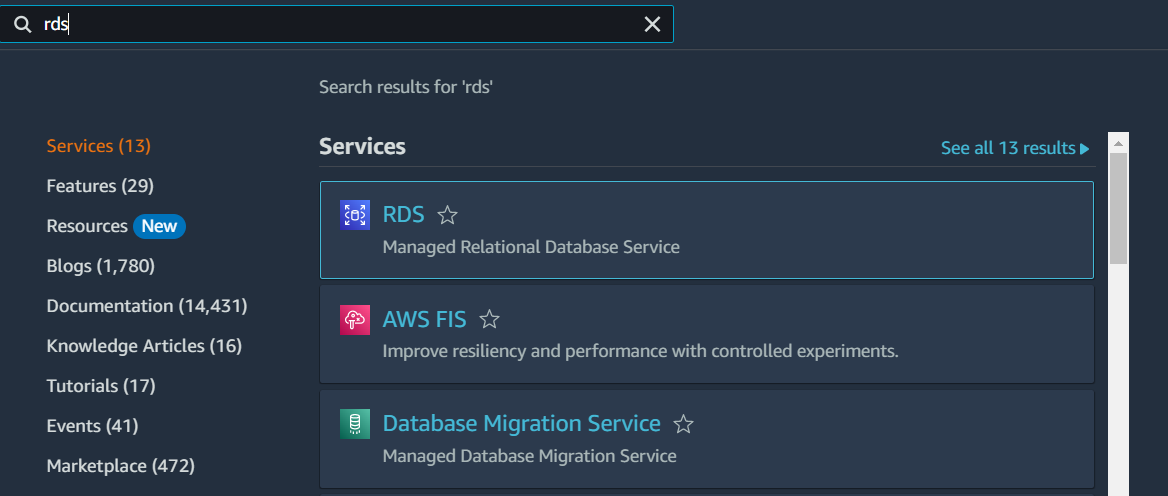
3. Click “Create Database”: On the RDS dashboard, click the “Create database” button.
4. Choose a database engine: Select the engine you want to use for your RDS instance. Amazon RDS supports various database engines like MySQL, PostgreSQL, Oracle, SQL Server, MariaDB, etc.
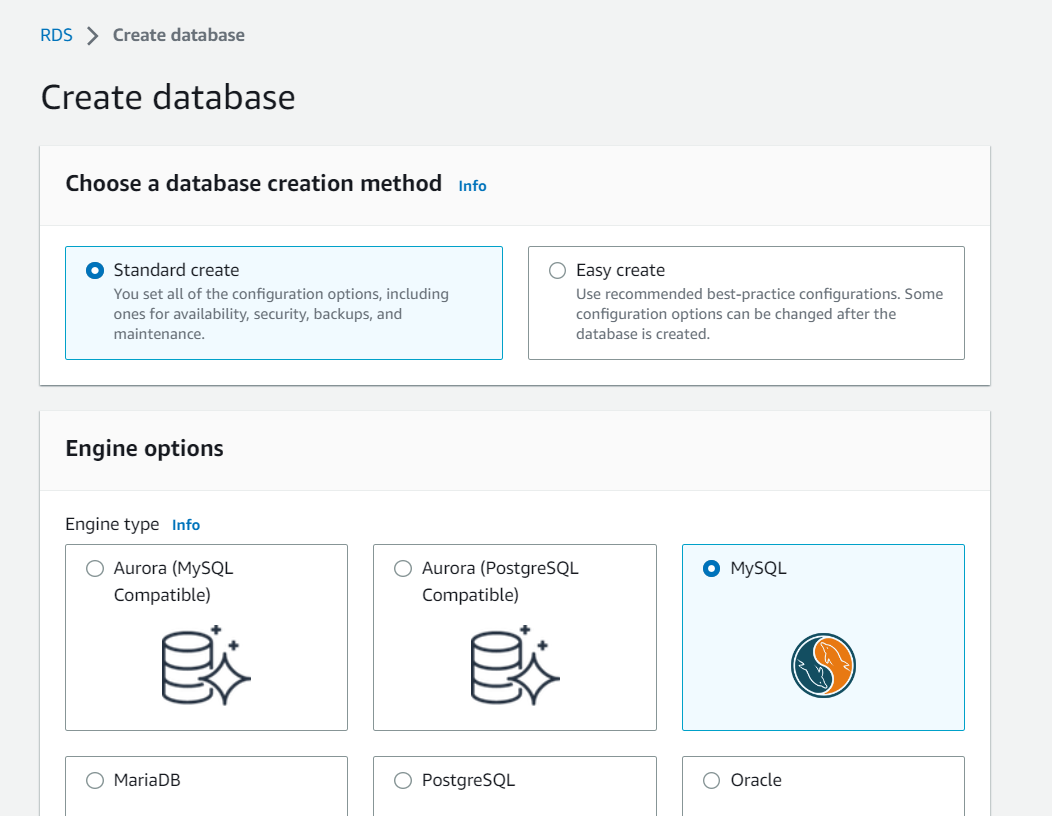
5. Choose a use case: Select the use case that best fits your needs. This will determine the default settings for your RDS instance, such as the instance class, storage type, and allocated storage.
6 . Configure the instance: Configure the RDS instance by specifying its name, username, and password. You can also choose the instance type, storage type, allocated storage, and other settings based on your requirements.
7. Configure advanced settings: If needed, you can configure advanced settings such as backup retention, maintenance window, security groups, and VPC settings.
8. Launch the instance: After configuring all the settings, review your configuration and click “Create Database” to launch your RDS instance.
9. Please wait for the instance to launch: It may take several minutes for your RDS instance to launch. Once it is ready, you can connect to it using the endpoint provided in the AWS Management Console.
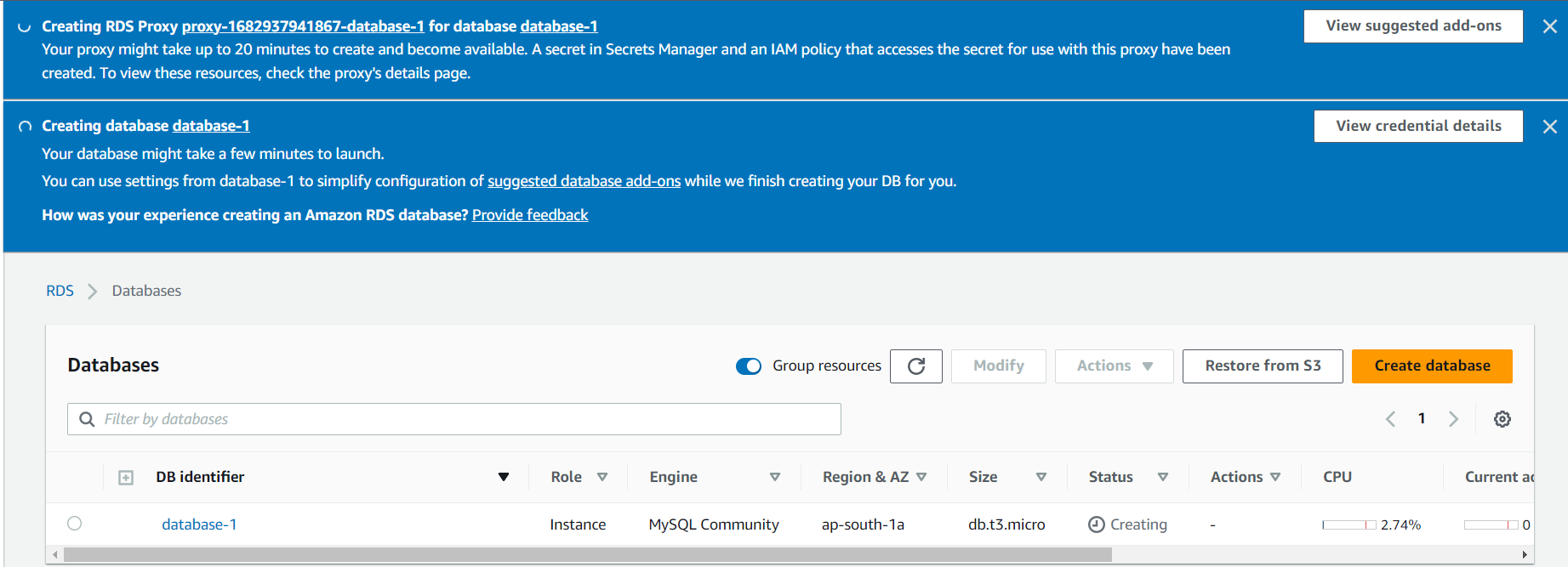
That’s it! You have now created an RDS instance in AWS. You can use this instance to host your database and connect to it from your applications.
IAM service policy
1. Open the IAM Management Console: Go to the AWS Management Console and log in to your AWS account. From the list of AWS services, choose “IAM” under “Security, Identity & Compliance”.
2. Create a new policy: In the left-hand navigation pane, click “Policies”, then click “Create policy”.
3. Select a policy template: On the Create Policy page, you can either create your custom policy or use a pre-defined policy template. To create a policy for RDS, you can select the “Amazon RDS” service from the list of available services.
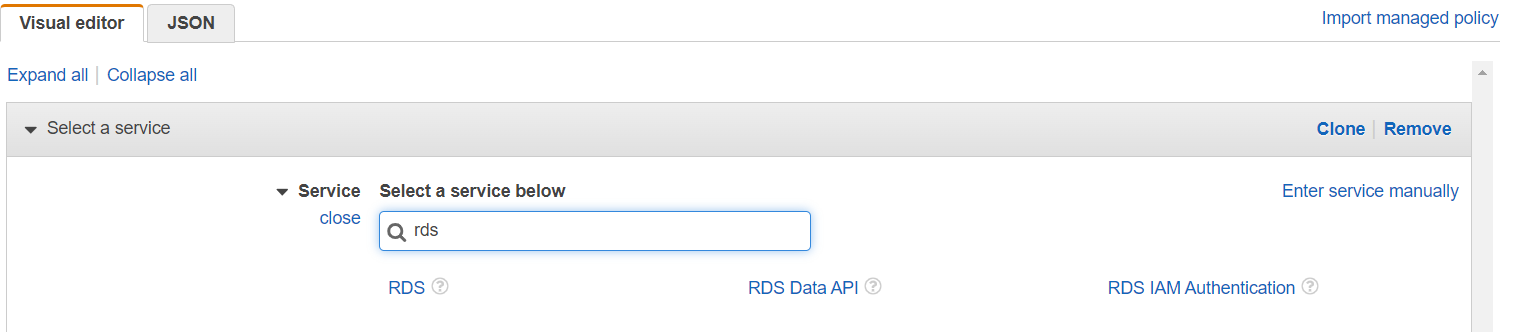
4. Choose the actions: Next, you need to choose the actions that you want to allow or deny for this policy. For example, you might want to allow read-only access to RDS resources or grant permissions to create and modify RDS resources.
5. Choose the resources: Once you have selected the actions, specify the RDS resources to which this policy applies. You can choose to apply the policy to all resources or specify individual resources by ARN (Amazon Resource Name).
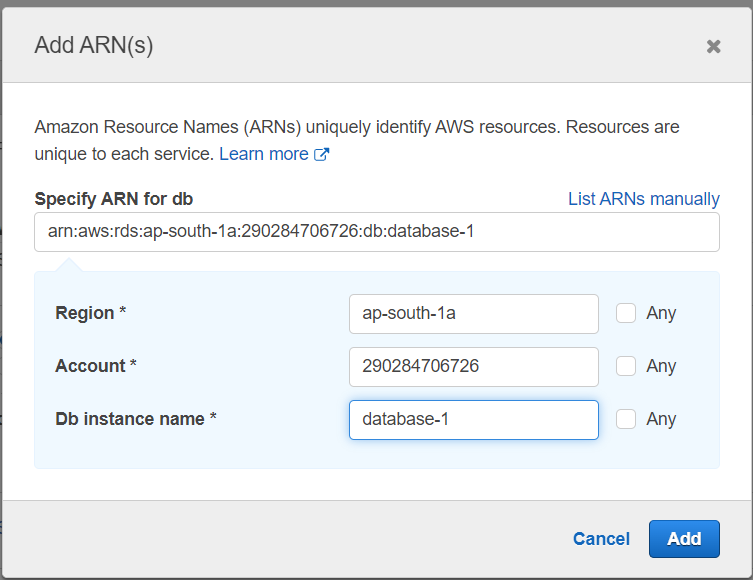
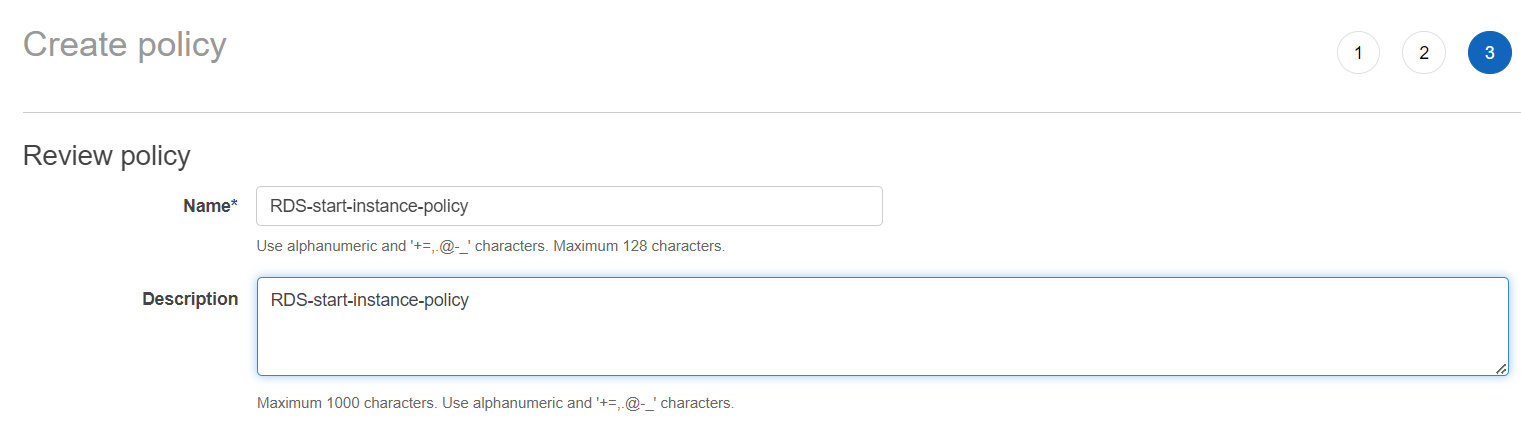
6. Review and create the policy: After specifying the actions and resources, review the policy details and click “Create policy” to save the policy.

7. Attach the policy to a user or group: Once you have created the policy, you need to attach it to a user or group that needs access to RDS resources. You can do this by navigating to the user or group in the IAM console, clicking on the “Permissions” tab, and then attaching the policy to the user or group.
That’s it! You have now created an IAM service policy for RDS and attached it to a user or group. The user or group can now perform the allowed actions on the specified RDS resources.
IAM service role
1. Navigate to the IAM dashboard.
2. Click on “Roles” from the left-hand menu.
3. Click on the “Create role” button.
4. Choose the type of trusted entity for your role: an AWS service, another AWS account, or a web identity provider.
5. Select the policies that define the permissions for your role. You can choose from existing policies or create a custom one.
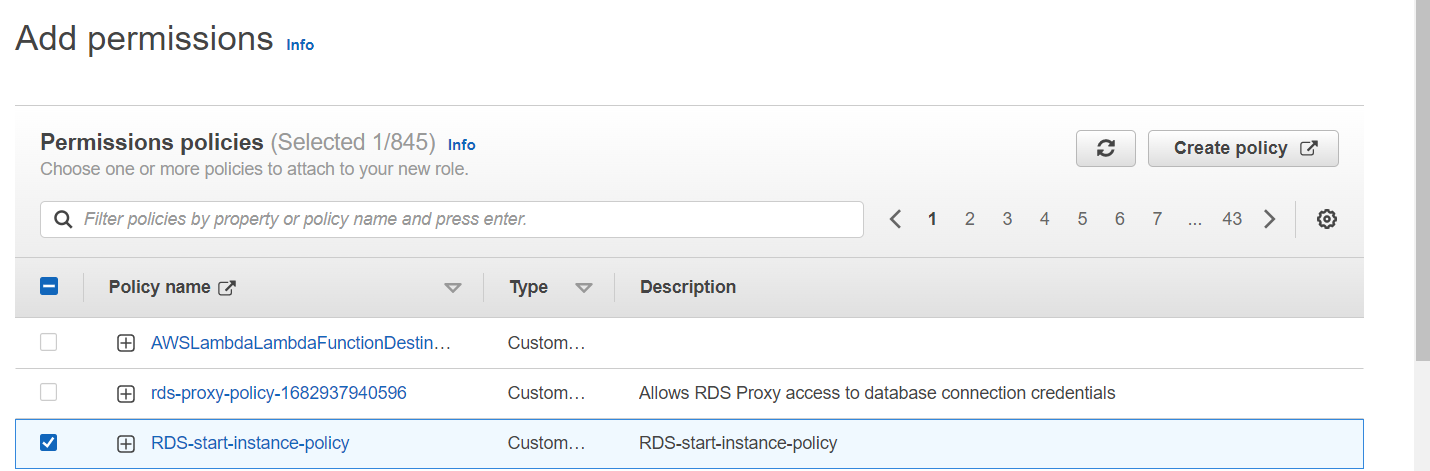
6. Give your role a name and description.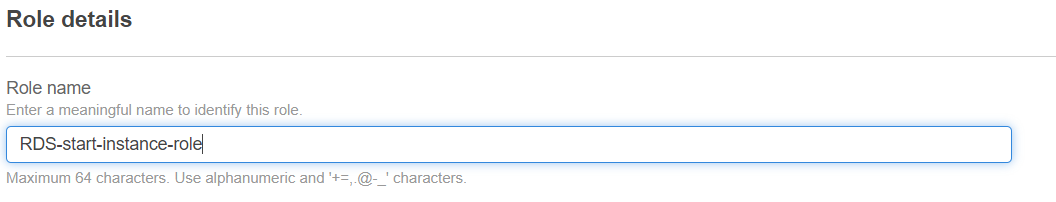
7. Review your role and click “Create role” to save it.

That’s it! You have now created an IAM service role in AWS. You can use this role to grant permissions to an AWS service or other entities that need to perform actions on your behalf.
Lambda function
1. Navigate to the Lambda dashboard.
2. Click on the “Create function” button.
3. Choose the type of function you want to create. You can create a function, blueprint, or serverless application repository from scratch.
4. Give your function a name and description.
5. Choose a runtime for your function, such as Python, Node.js, or Java.
6. Configure the function’s execution role, which determines the permissions that the function has to access AWS resources.
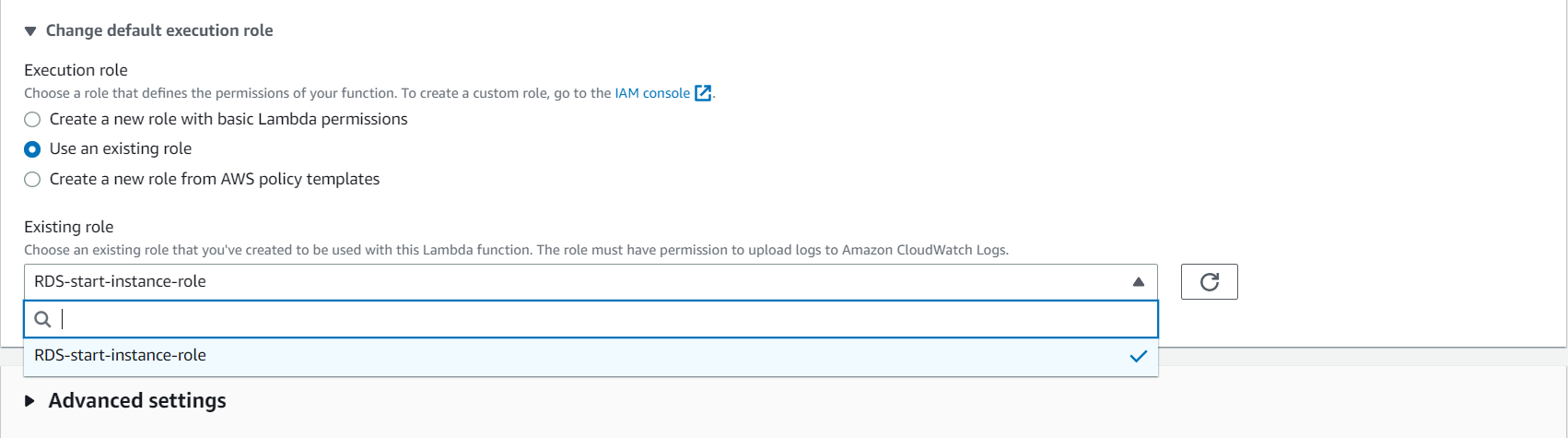
7. Write your function code or upload a ZIP file containing your code.
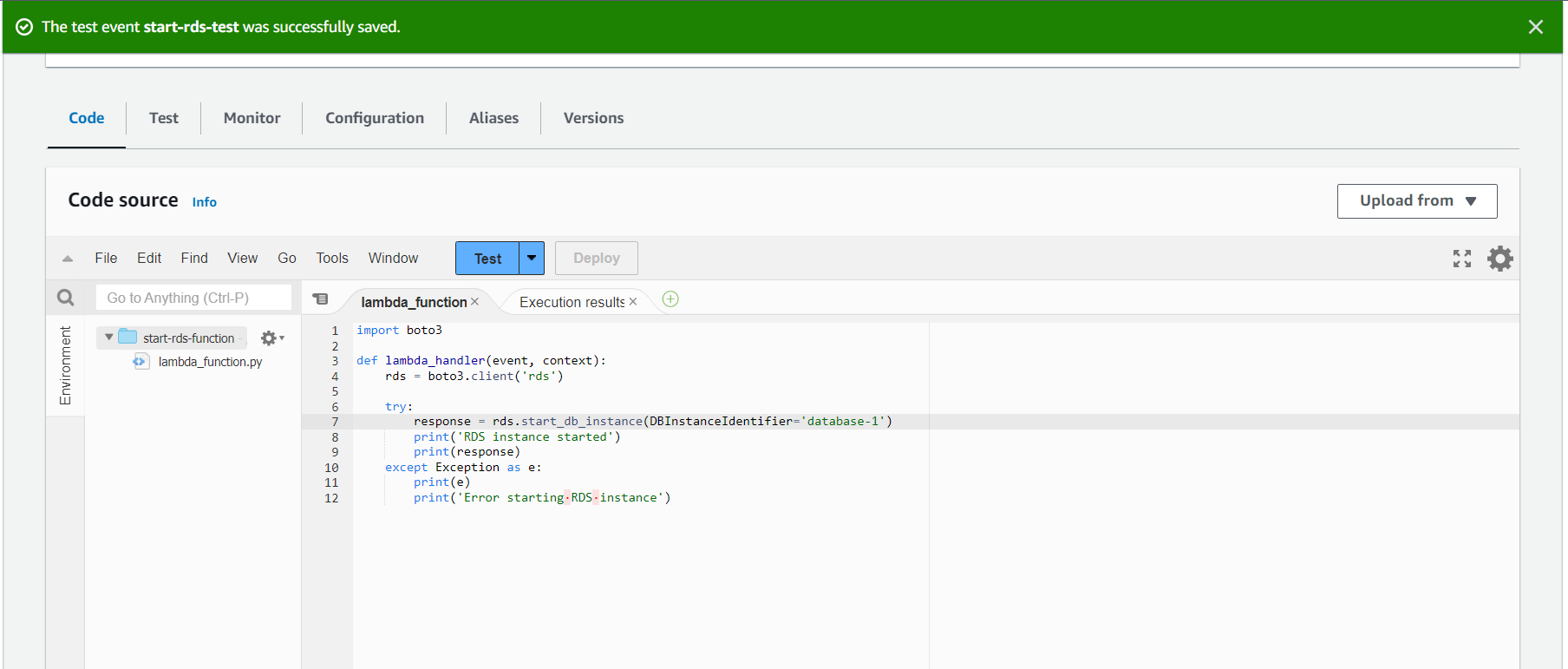
8. Set up your function’s environment variables and any additional settings, such as memory and timeout settings. Click “Create function” to save your Lambda function.
After creating your Lambda function, you can test it manually or set up a trigger to invoke it automatically. You can also monitor your function’s performance and troubleshoot any errors using the AWS Lambda console.
CloudWatch
1. Navigate to the CloudWatch dashboard.
2. Click on “Events” from the left-hand menu.
3. Click on the “Create rule” button.
4. Choose the “Schedule” option under “Event Source”.
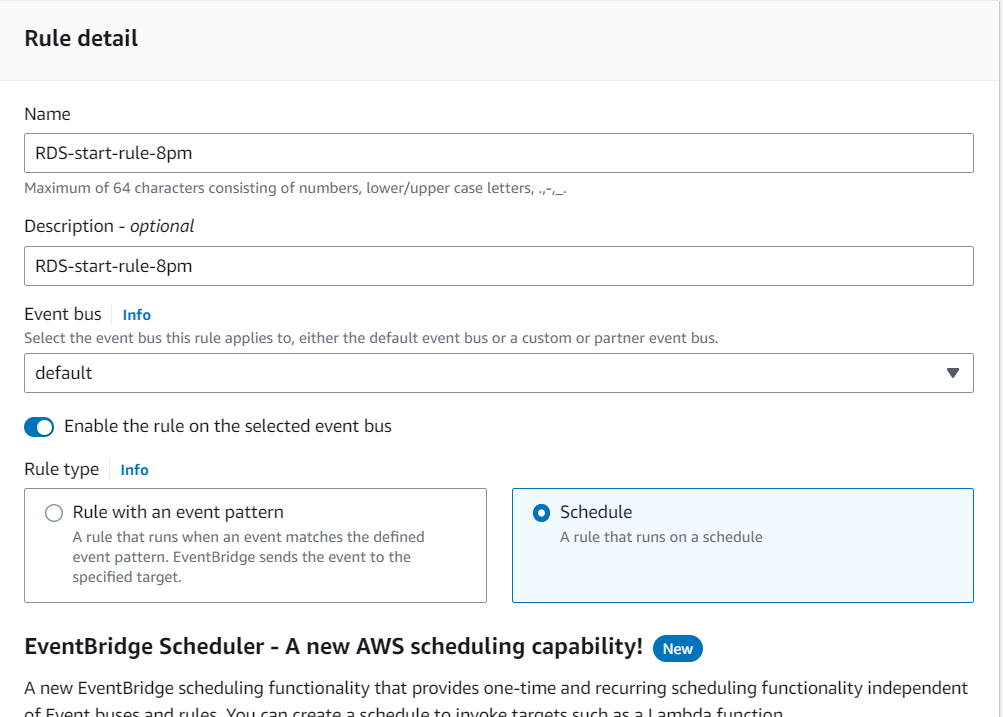
5. Configure the croon expression for when you want the RDS DB instance to start. For example, if you want it to start every day at 8 pm, you would use the expression 25 5 * *? *
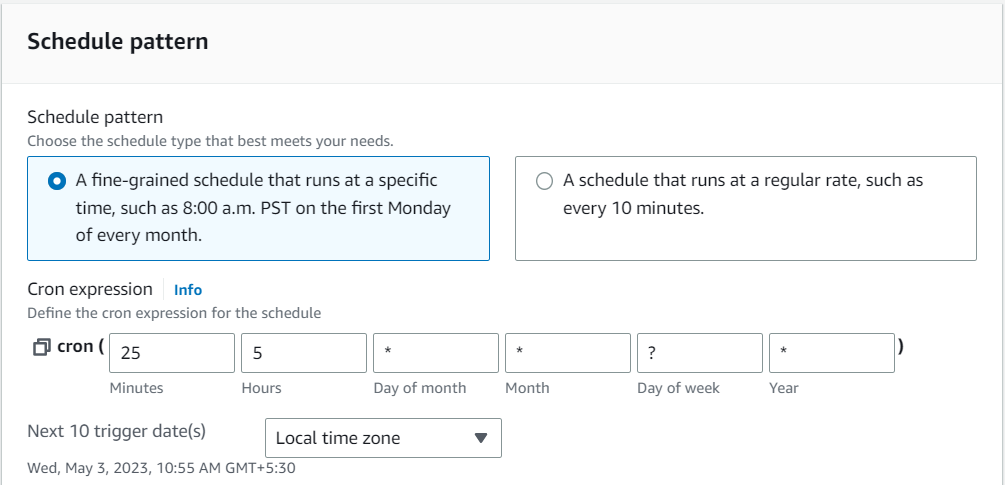
6. Choose the EC2 instance as the target for the event rule.
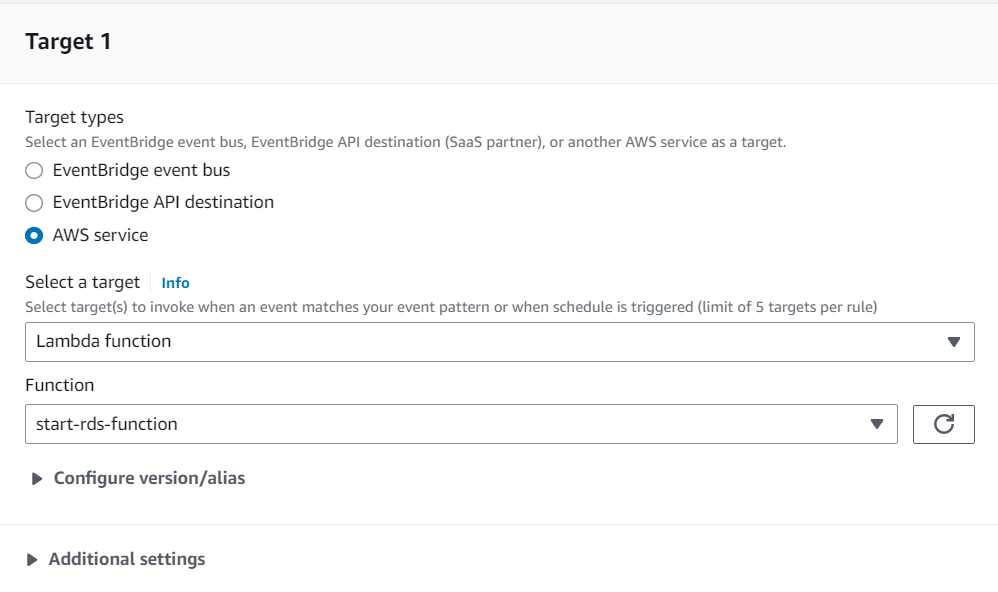
7. Configure the specific action that you want to perform on the RDS DB instance, which in this case is to start it.
8. Give your rule a name and description.
9. Click “Create rule” to save your CloudWatch event rule.

After creating your CloudWatch event rule, it will trigger at the scheduled times and start the specified EC2 instance. Be sure to test your rule to ensure it is working as expected.
STOP THE RDS DB INSTANCE
1. creating IAM policy
2. creating IAM role
4. creating Lambda function RDS-stop-instance and attaching a role
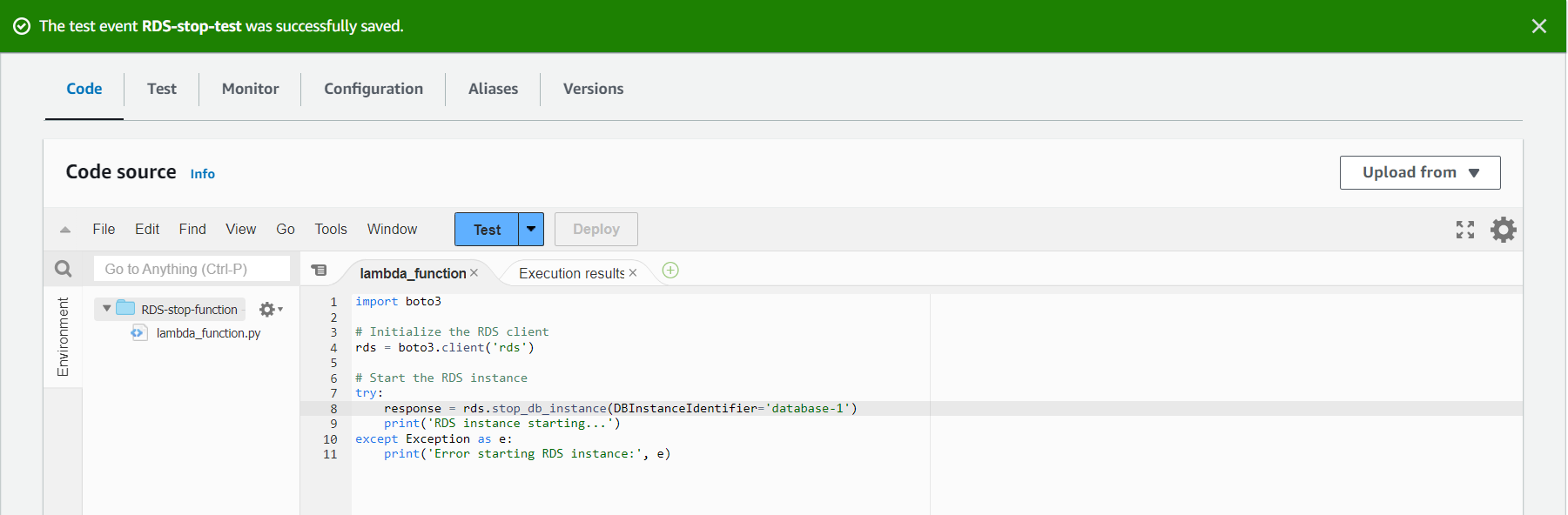
8. creating CloudWatch Choose the “Schedule” option under the “Event Source” rule.
9. Configure the croon expression for when you want the RDS DB instance to s. For example, if you want it to start every day at 8 pm, you would use the expression 10 6 * *? *
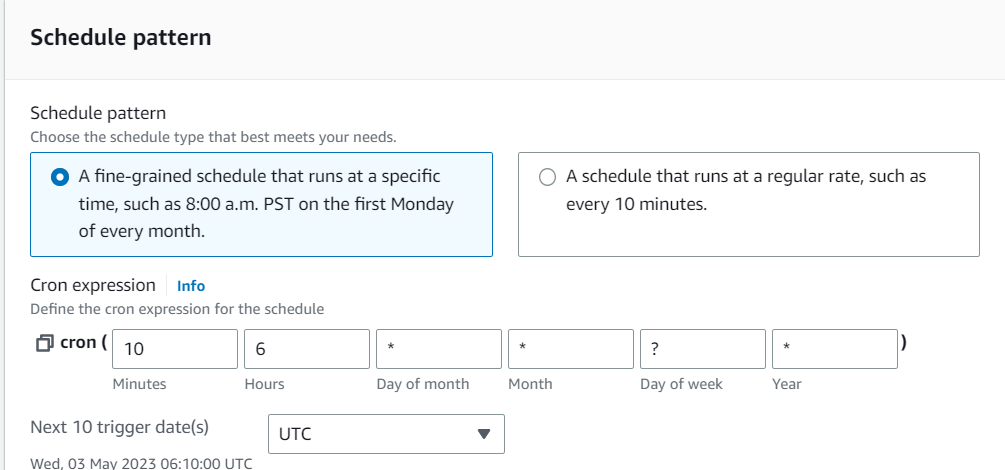
successfully RDS starts to stop the instance