- AWS
- AWS Training and Certification
- Cloud Computing
- Docker and Kubernetes
- IT Training and Certification
- linux
First, we need to create an s3 Bucket steps are given below:
To bucket create
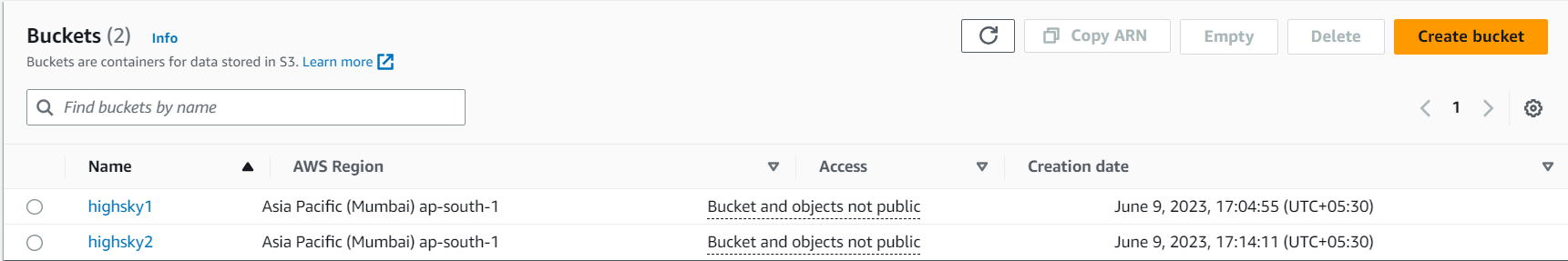
1 highsky1
2 highsky2
1 ( highsky1 )
Step 1: Log on to your AWS Console.
Step 2: go to the Search bar ” S3 services “
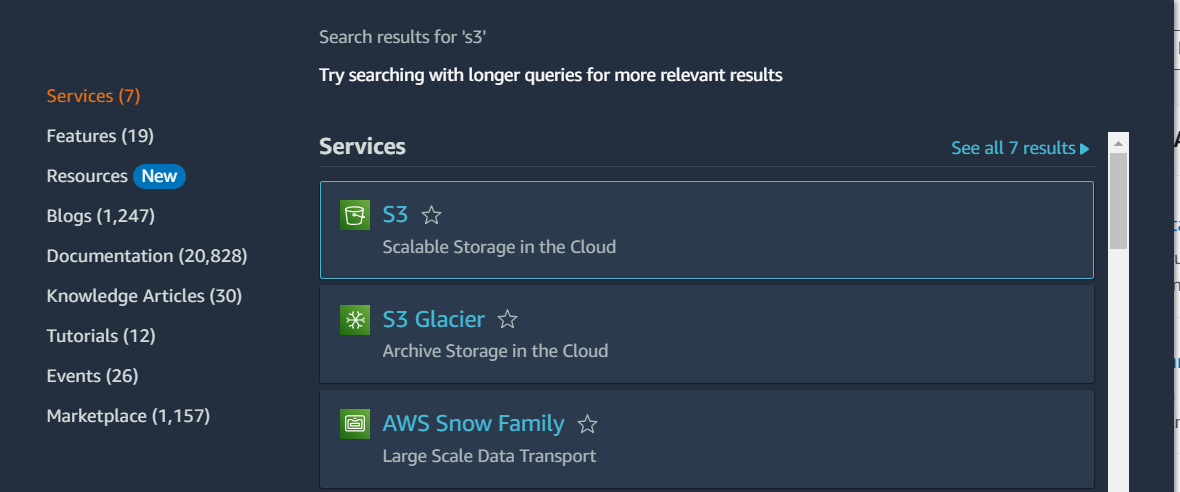
Step 3: Click on S3 Scalable Storage in the Cloud” and proceed further
Step 4: Create a new Bucket
In the general configuration category:
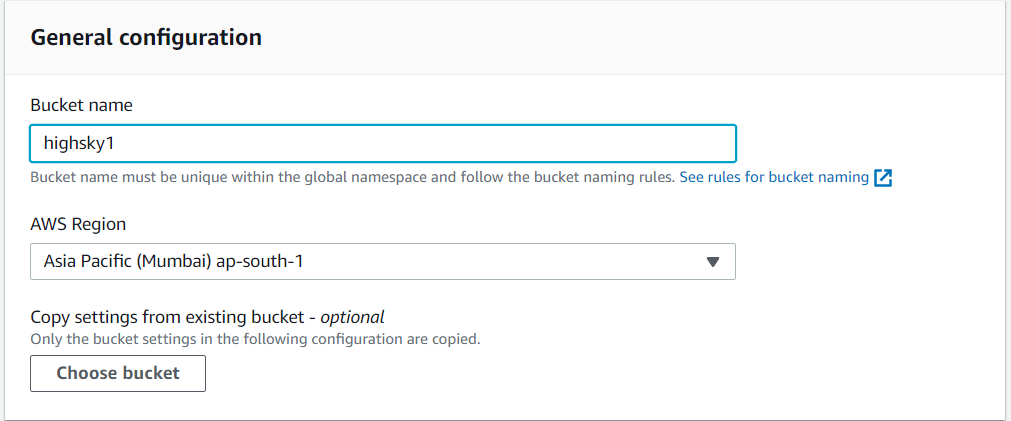
Step 5: Enter the bucket name ( highsky1 )
Step 6: Next, choose the AWS region, [Asia Pacific (Mumbai) ap-south-1].
ACLs disabled (Recommended)
Bucket owner enforced – Bucket and object ACLs are disabled, and you, as the bucket owner, automatically own and have full control over every object in the bucket. Access control for your bucket and the objects in it is based on policies such as AWS Identity and Access Management (IAM) user policies and S3 bucket policies Objects can be uploaded to your bucket only if they don t specify an ACL or if they use the bucket-owner-full-control canned ACL.
Block Public Access settings for this bucket
Public access is granted to buckets and objects through access control lists (ACLs), bucket policies, access point policies, or all. In order to ensure that public access to this bucket and its objects is blocked, turn on Block all public access. These settings apply only to this bucket and its access points. AWS recommends that you turn on Block all public access, but before applying any of these settings, ensure that your applications will work correctly without public access. If you require some level of public access to this bucket or objects within, you can customize the individual settings below to suit your specific storage use cases
Bucket Versioning
Versioning is a means of keeping multiple variants of an object in the same bucket. You can use versioning to preserve, retrieve, and restore every version of every object stored in your Amazon S3 bucket. With versioning, you can easily recover from both unintended user actions and application failures.
Disable
( choose the Disable )
Default encryption
The default encryption configuration of an S3 bucket is always enabled and is at a minimum set to server-side encryption with Amazon S3-managed keys (SSE-S3). With server-side encryption, Amazon S3 encrypts an object before saving it to disk and decrypts it when you download the object. Encryption doesn’t change the way that you access data as an authorized user. It only further protects your data. You can configure default encryption for a bucket. You can use either server-side encryption with Amazon S3 managed keys (SSE-S3) (the default) or server-side encryption with AWS Key Management Service (AWS KMS) keys (SSE-KMS).
Amazon S3 managed keys (SSE-S3)
Bucket Key = Enabel
Step 7: Click on Create Bucket.
If the bucket is created successfully, you will see a message like this on the top of the page:

2 ( highsky2 )

2 Creating an IAM (Identity and Access Management) service in AWS (Amazon Web Services) can be done by following these steps:
( 1 Create a Policy ) 2 ( Create User )
1 Create Policy
( 1 ) Go to the IAM service by searching for it in the search bar or selecting it from the list of services.
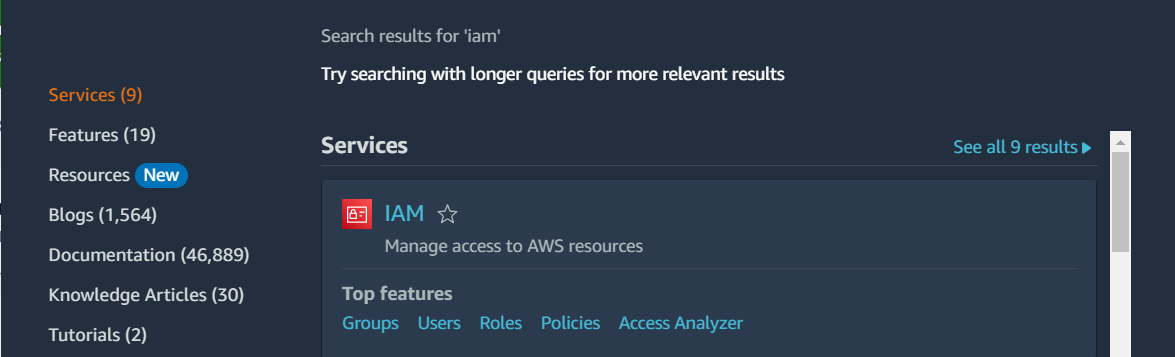
1. Go to the IAM service by searching for it in the search bar or selecting it from the list of services.
2. Once in the IAM console, click on the “Policies” tab in the left-hand menu.
3. Click the “Create policy” button.
4. Choose either the “Visual editor” or the “JSON” tab to create the policy.
5. choose the Visual editor tab to select the service the policy will apply to and then choose the actions and resources the policy will allow or deny
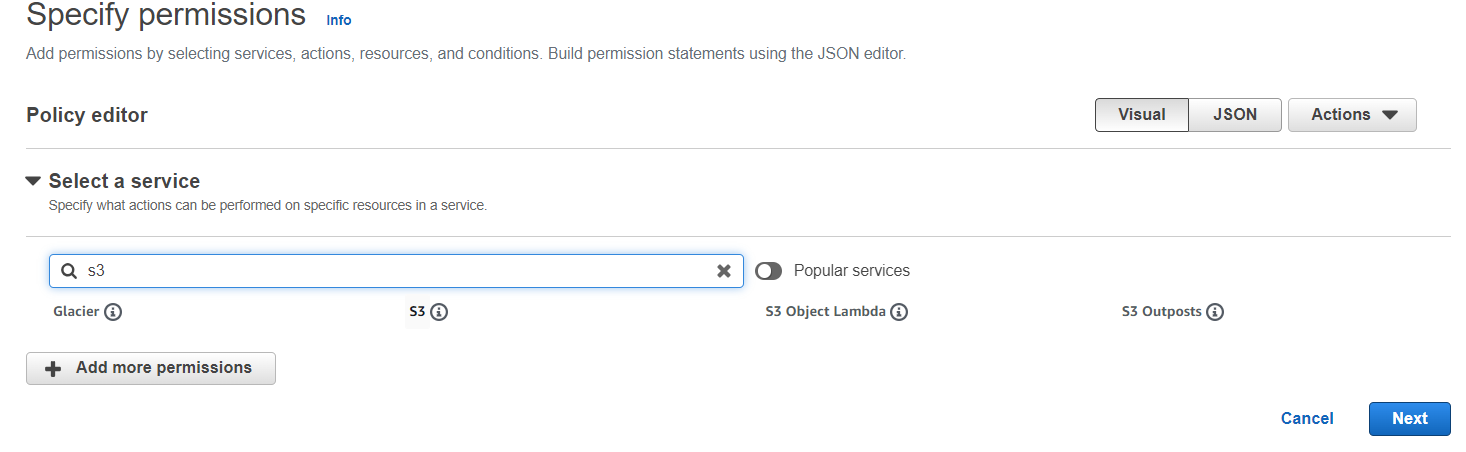
( 1 ) Select the “JSON” tab.
( 2 ) Define the policy document using the JSON syntax. The policy document specifies the permissions and resources that the policy grants or denies.
( 3 ) Make sure to include the necessary actions, resources, and conditions according to your requirements.
( 4 ) Click on the “Review policy” button.
( 5 ) Provide a name and optional description for your policy.
( 6 ) Review the policy details and click on the “Create policy” button to finalize it.
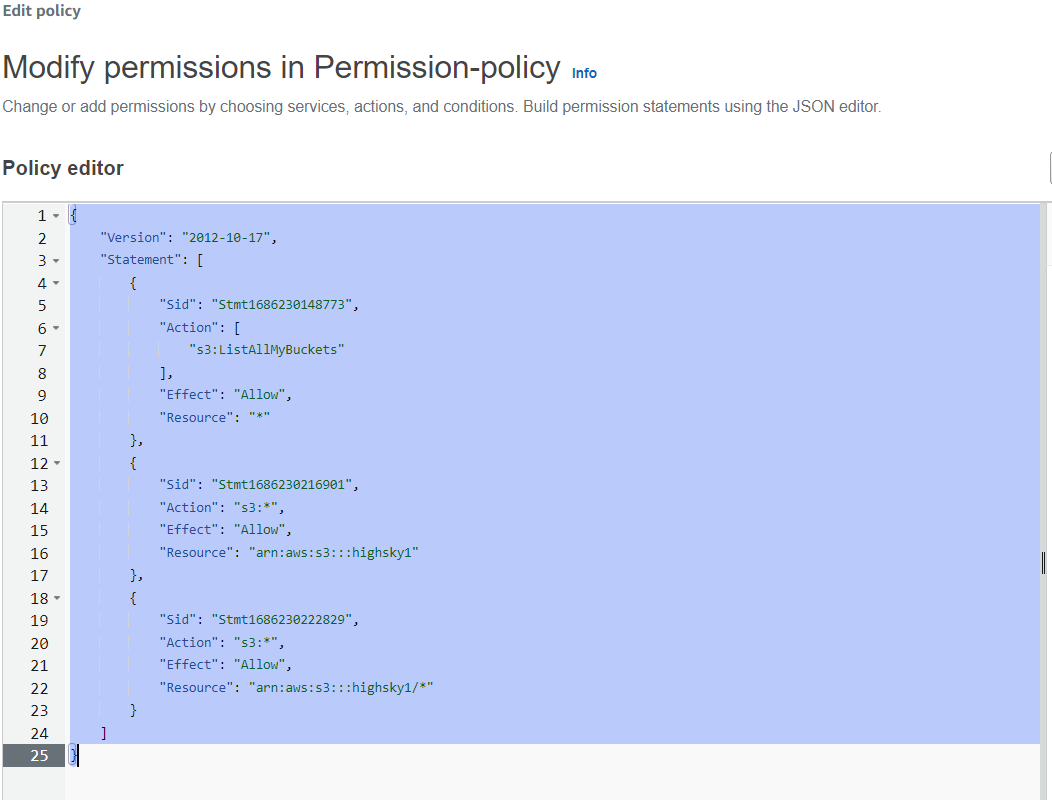
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Stmt1686230148773",
"Action": [
"s3:ListAllMyBuckets"
],
"Effect": "Allow",
"Resource": "*"
},
{
"Sid": "Stmt1686230216901",
"Action": "s3:*",
"Effect": "Allow",
"Resource": "arn:aws:s3:::Your Bucket Name "
}
{
"Sid": "Stmt1686230222829",
"Action": "s3:*",
"Effect": "Allow",
"Resource": "arn:aws:s3:::Your Bucket Name /*"
}
]
}
Click Next
Full permission in Bucket ( highsky1 )
( 7 ) Policy Name File ( permission-policy )
And Click ( Create policy )
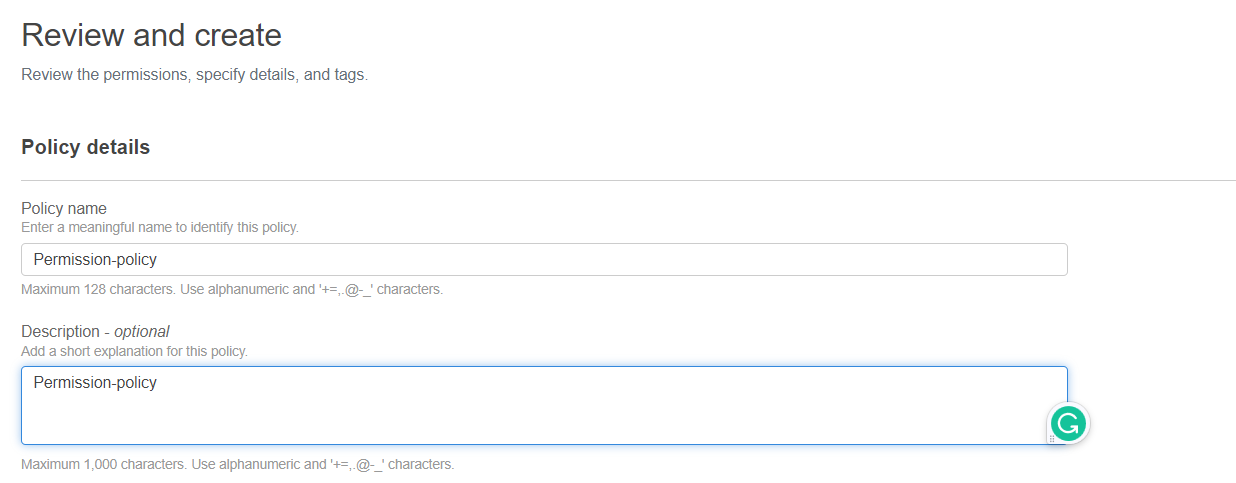

Once the policy is created, you can attach it to a user, group, or role in IAM. When the user, group, or role tries to access a resource, the policy will be checked to determine whether the action is allowed or denied.
It’s important to test your policy to ensure that it’s providing the intended access and restrictions. can do this by using the Simulate policy feature in the IAM console, which lets you simulate a policy to see how it would apply in different scenarios
2 Create User
1. Once in the IAM console, click on the “Users” tab in the left-hand menu.
2. Click the “Add user” button.
3. Enter a name for the new user and select the “Programmatic access” checkbox to give the user access to AWS via APIs, CLI, and SDKs.
4. Password ( Harry@123 )
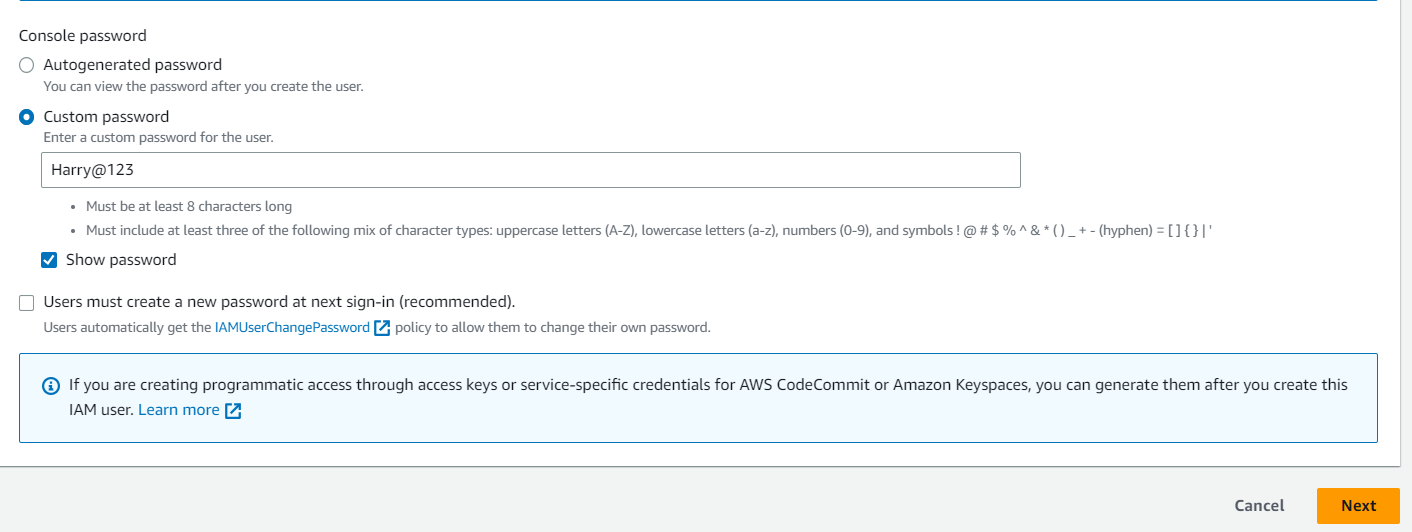
5. Click “Next: Permissions” to assign the user permissions.
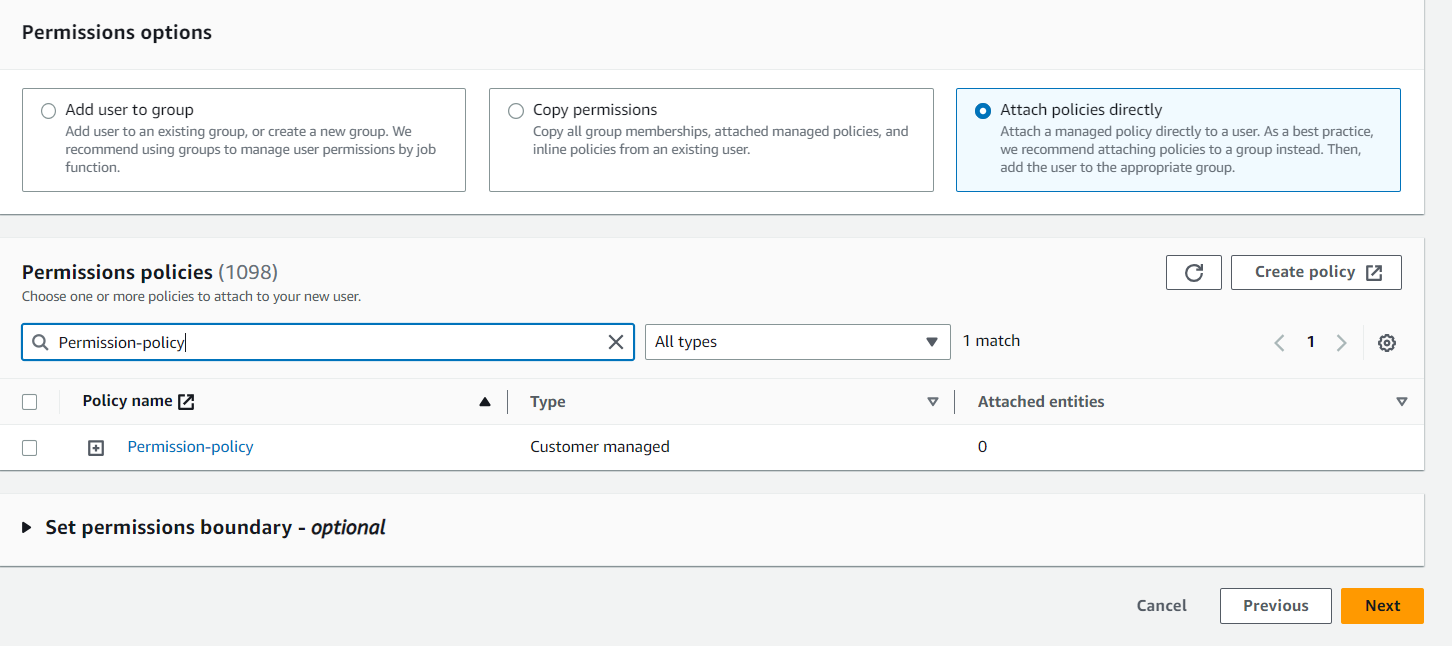
Click ( Next )
6. Click Create User to create a new user.
Once the user is created, you’ll be provided an Access Key ID and a Secret Access Key, which you can use to programmatically access AWS services. Be sure to keep these credentials safe, as they provide access to your AWS resources.
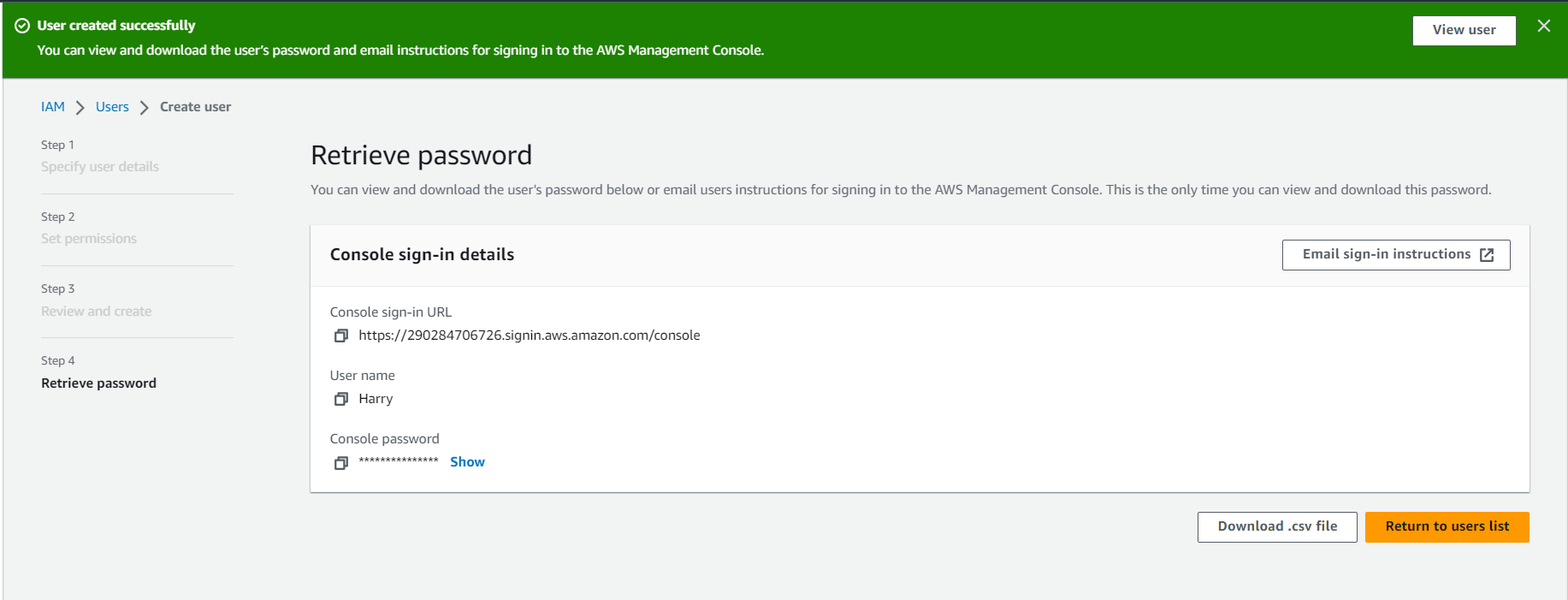
Click Download .csv file
Login Harry user
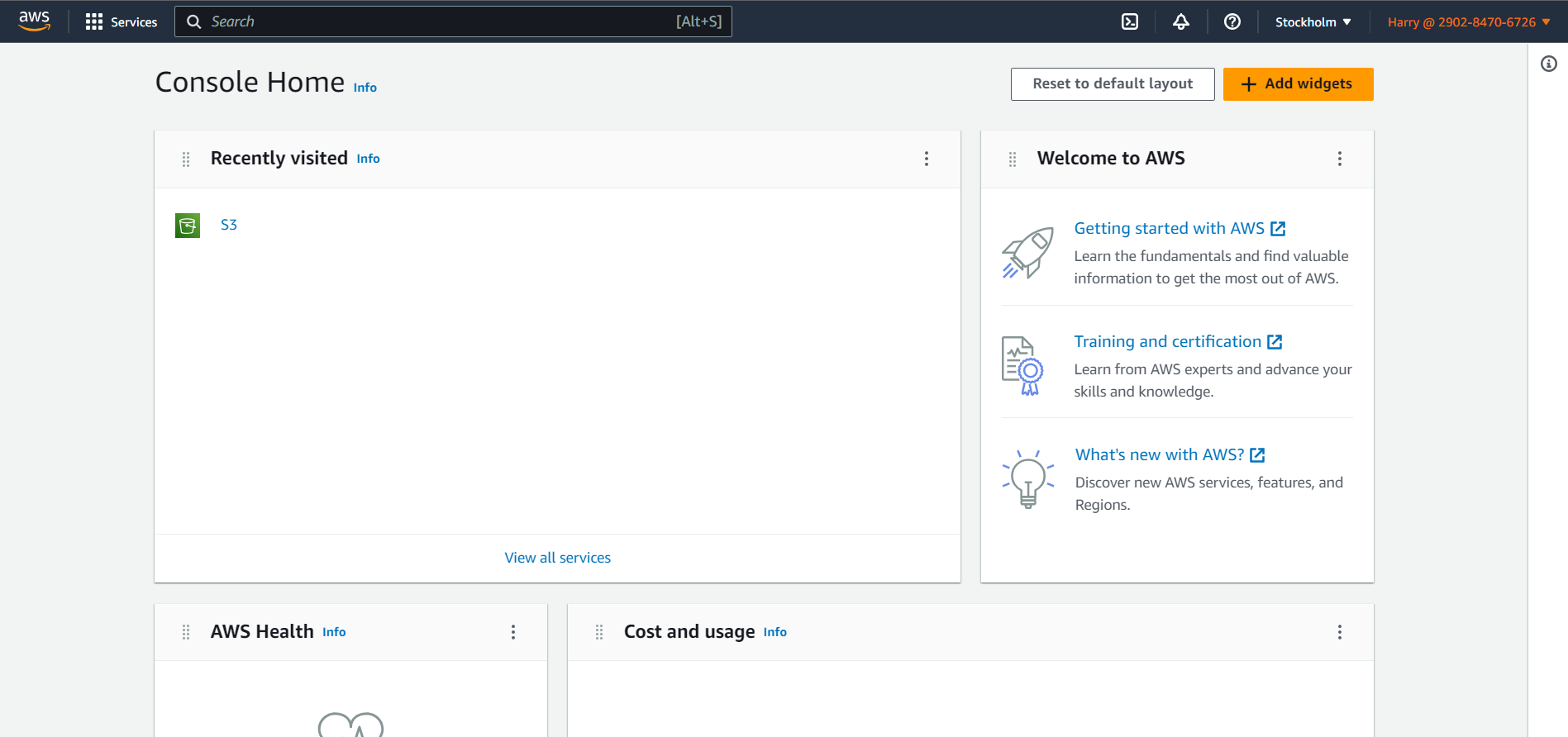
Go To the S3 service
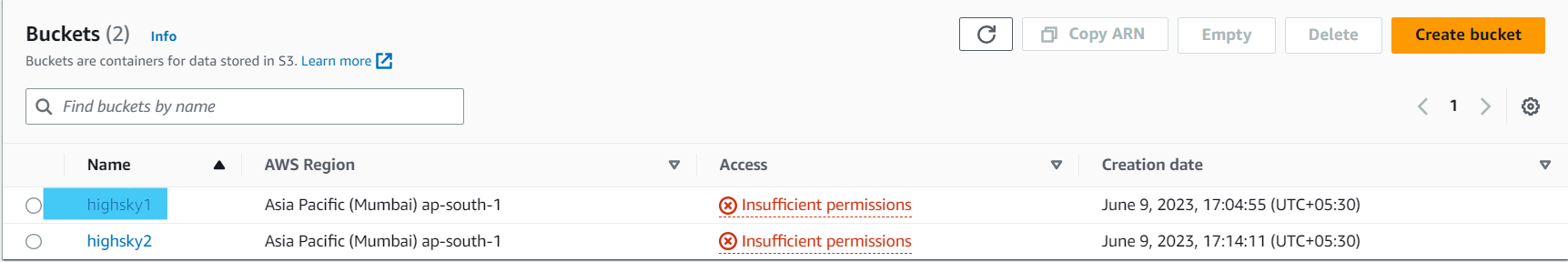
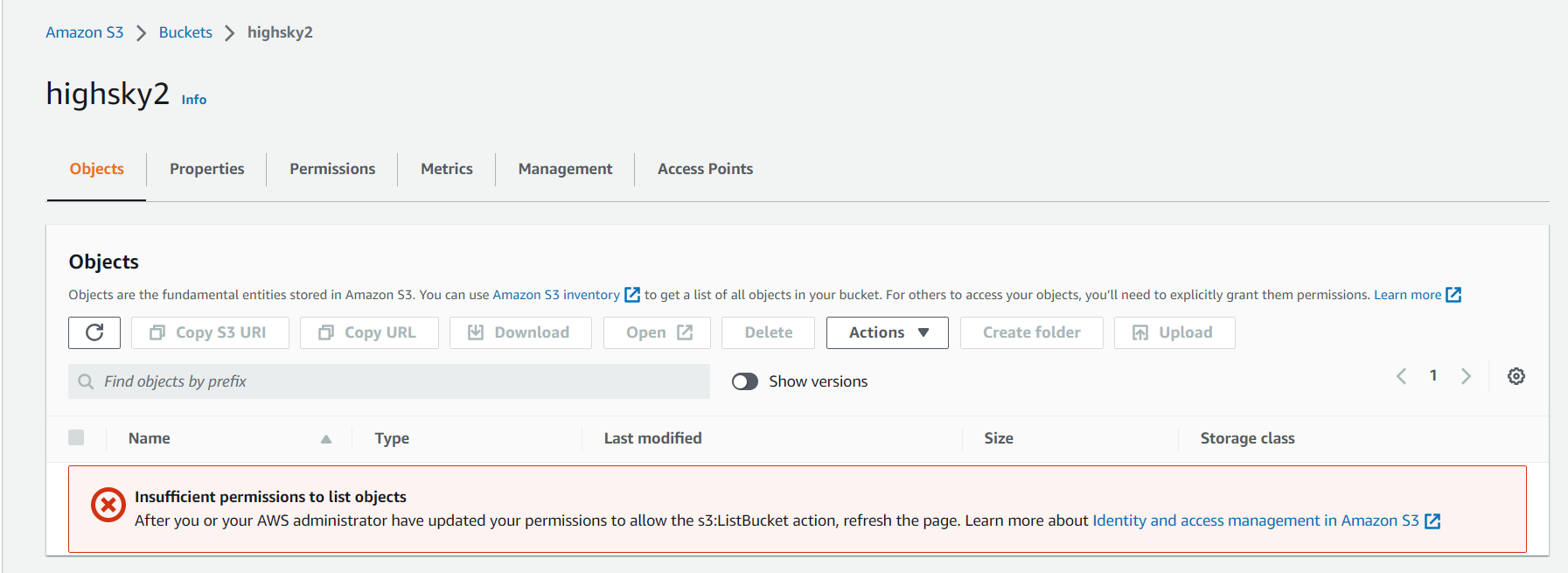
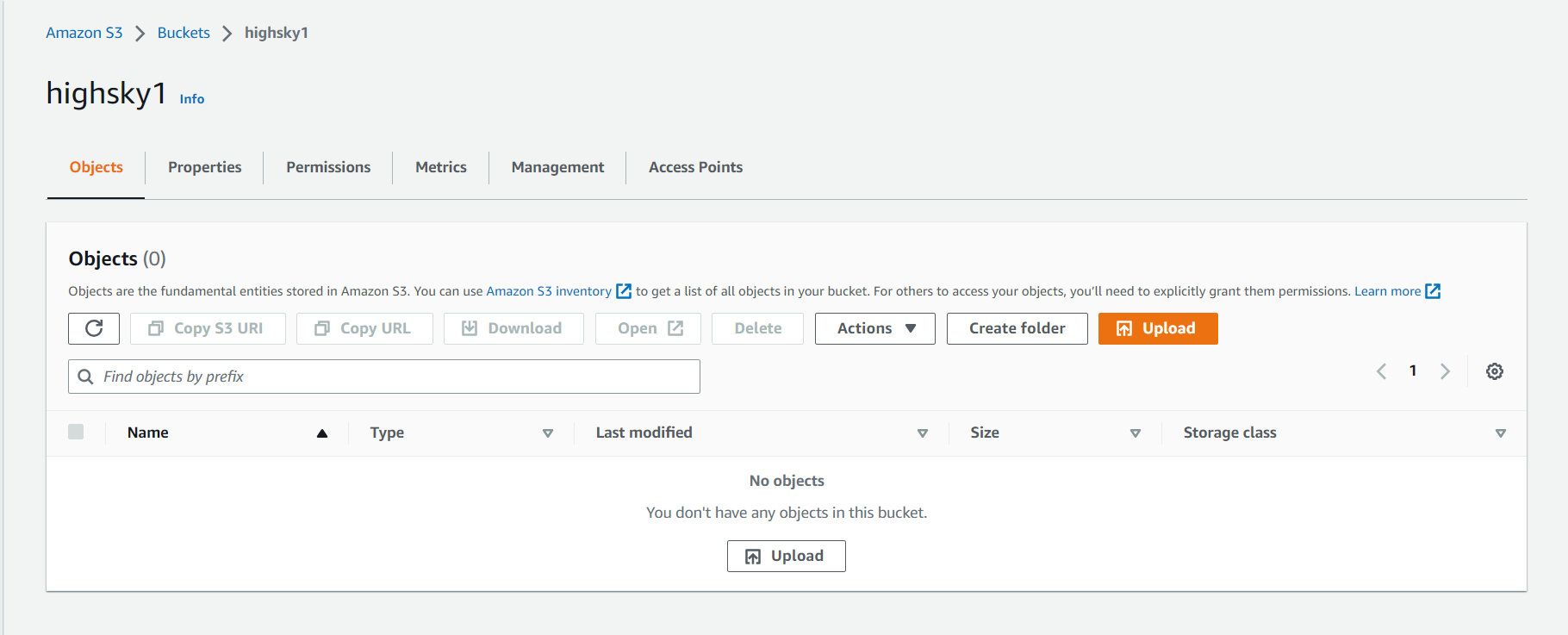
1 highsky1 ( He has full permission, he can upload data in this and also delete )
2 highsky2 ( Can See And Do Nothing )